Exploring Peebles, Scotland: History, Culture, and the Charm of the Borders Town
Introduction to Peebles: A Scottish Gem in the Borders
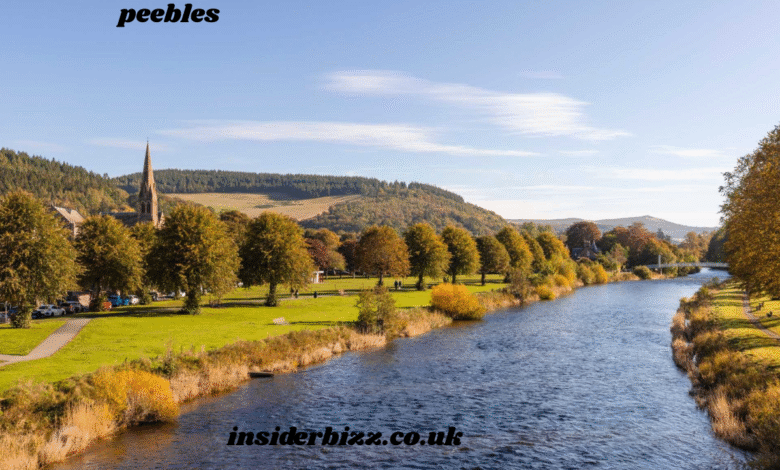
Nestled in the scenic countryside of the Scottish Borders, Peebles stands as a town rich in history, natural beauty, and cultural significance. Located along the banks of the River Tweed, Peebles has grown from its early medieval roots into a vibrant market town that continues to captivate residents and visitors alike. Whether one is drawn by its architectural heritage, bustling high street, or the therapeutic landscapes of nearby glens and hills, Peebles offers a uniquely Scottish experience full of warmth, history, and charm.
Historical Origins of Peebles: From Royal Burgh to Cultural Hub

Peebles was established as a Royal Burgh in the 12th century by King David I of Scotland, solidifying its importance as a trading and strategic center. The town’s name is believed to be derived from the Brythonic word “pebyll,” meaning “tent” or “pavilion,” indicating that the area may have served as a gathering point or military encampment in ancient times. Over the centuries, Peebles became well known for wool production and tweed textiles, thanks to the abundance of sheep farming in the surrounding hills.
In medieval times, Peebles was a fortified settlement, and parts of the old town walls and towers still hint at its defensive past. Historic landmarks such as the Cross Kirk, founded in 1261, continue to tell the story of Peebles’ ecclesiastical significance and monastic influence.
Peebles Today: A Blend of Tradition and Modern Life
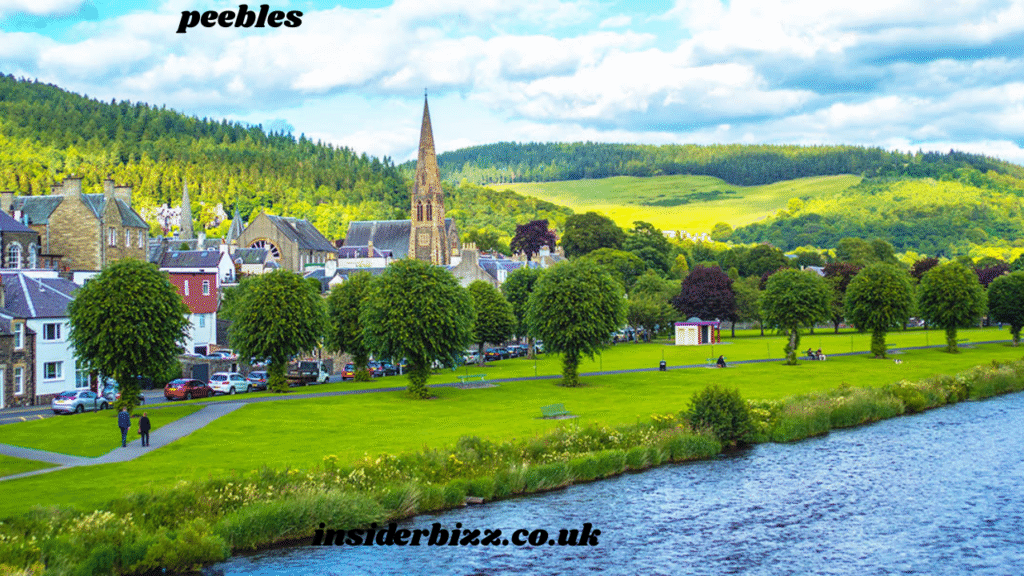
In contemporary times, Peebles balances its historical heritage with a thriving modern community. The High Street remains the heart of the town, lined with independent shops, cozy cafes, family-run businesses, and cultural venues. From handmade crafts to gourmet food, Peebles maintains its reputation as a center for local enterprise and creativity.
The town also boasts excellent educational institutions, public amenities, and residential communities, making it a desirable place to live for families and retirees. Despite its growth, Peebles retains a distinct sense of identity and community spirit that continues to draw people in.
Architectural Landmarks and Natural Wonders

One of the defining features of Peebles is its harmonious blend of built and natural environments. The town features a range of architectural styles, from medieval ruins to elegant Georgian houses and Victorian-era buildings. Noteworthy landmarks include:
- Neidpath Castle: A partially restored fortress that dates back to the 14th century, located just west of the town.
- Tweed Bridge: The historic stone bridge over the River Tweed, which has provided a crossing point for centuries.
- Old Parish Church: An enduring symbol of the town’s ecclesiastical history.
Peebles is also surrounded by spectacular landscapes. The Glentress Forest, part of the Tweed Valley Forest Park, offers hiking, mountain biking, and nature-watching. The River Tweed itself is famed for salmon fishing, attracting anglers from across the globe.
Peebles and the Arts: A Cultural Beacon in the Borders
Peebles has long had a connection to the arts. The Eastgate Theatre and Arts Centre serves as the cultural heartbeat of the town, hosting performances ranging from drama and music to film and contemporary art exhibitions. Local festivals, such as the Beltane Festival, celebrate both ancient tradition and modern creativity with parades, concerts, and communal celebrations.
Artisans and creatives also call Peebles home, making it a haven for painters, writers, and musicians. The surrounding natural beauty continues to inspire works that contribute to the cultural tapestry of the Scottish Borders.
Events and Festivals: The Pulse of Peebles Community Life
Peebles is well-known for its calendar of annual events that draw visitors and locals together in celebration. Key highlights include:
- Peebles Beltane Week: A unique traditional festival dating back to pagan times, featuring a crowning of the Beltane Queen, procession of floats, and community-wide festivities.
- Tweeddale Agricultural Show: Showcasing local livestock, crafts, and rural traditions.
- Peebles Arts Festival: A week-long showcase of visual arts, music, and literature.
These events reinforce the town’s strong sense of community, and provide platforms for intergenerational exchange and regional pride.
Economy and Local Industry in Peebles
While tourism plays a major role in the economy of Peebles, the town also benefits from small-scale manufacturing, agriculture, and professional services. The legacy of the textile industry still echoes in some local businesses, and there is a growing focus on sustainable enterprises and eco-tourism.
The weekly farmers’ market and high-street shops offer local produce, crafts, and goods that support a circular economy within the town. Entrepreneurs and small business owners find a supportive environment in Peebles, helping to sustain economic diversity.
Educational and Social Life in Peebles
Education is a pillar of life in Peebles, with well-rated primary and secondary schools that serve the community. The town encourages lifelong learning through community libraries, adult education programs, and youth clubs.
Peebles also has a robust social infrastructure. Recreational facilities such as swimming pools, sports fields, tennis courts, and mountain biking trails contribute to a healthy lifestyle. Several local organizations and charities help foster social cohesion, supporting both the young and elderly.
Tourism in Peebles: A Favorite Scottish Getaway
Visitors come to Peebles not only for its beauty but for the slow pace of life it offers compared to larger cities. The town is a popular destination for weekend escapes and longer holidays, especially for those exploring the Scottish Borders.
Local accommodations range from cozy B&Bs to luxury hotels, and the town is well-connected via road and bus networks, making it easy to reach from Edinburgh and other Scottish cities. Nature lovers, history buffs, and culture seekers all find something special in Peebles.
Peebles in Literature and Legacy
Peebles has been immortalized in literature, most notably by John Buchan, author of The Thirty-Nine Steps, who spent part of his youth in the area. His writings often reflect the terrain and ambiance of the Scottish Borders, particularly the sense of adventure that places like Peebles evoke.
The town’s literary and historical associations only add depth to its identity, making it a place not just of beauty but of intellectual and cultural legacy.
Conclusion: The Timeless Appeal of Peebles
Peebles stands as a testament to the enduring charm of Scottish Borders life. With its roots in medieval history, its rich cultural life, and its breathtaking natural surroundings, the town continues to thrive while preserving its heritage. Whether you are seeking adventure, relaxation, or inspiration, Peebles offers a multidimensional experience that is both memorable and enriching.
As Scotland continues to develop, Peebles remains a town that honors the past while embracing the future—making it a truly timeless gem in the heart of the Borders.
Also Read : India Gate: A Timeless Monument of National Pride



